In the last chapter, we talked about VPCs, and how a VPC is a private network inside AWS. It's like a big bubble of protection that we've built around our instances.
There are other people using AWS, and some of them might be bad people who want to connect to our instances and steal our data. But our instances are in a private network that no one else can get into.
If you haven't read the chapter on VPCs,
The benefit of having a protective bubble is that no one can connect to our instances. The downside of having a protective bubble is that no one can connect to our instances! We're building a website, after all, aren't we? How's anyone supposed to connect to our servers with this darned bubble in place?
We need to poke a hole in our bubble so we can talk to the internet.
Internet Gateways
An internet gateway is like a hole you poke in your VPC so you can talk to the internet.
Simple.
End of section.
Terraform code:
resource "aws_internet_gateway" "igw" {
vpc_id = aws_vpc.main.id
}Now you have an internet gateway (aka an IGW, pronounced "igwoo"). Here's what we have so far:
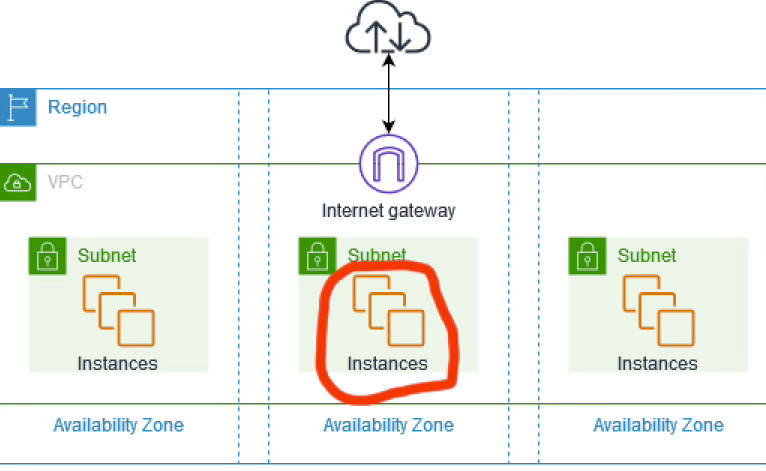
Here's what the internet gateway looks like in the AWS docs:
Let's zoom in:
Zoom in some more:
Beautiful. Like the Gateway of India, but online.
So now we have an internet gateway (IGW), we can connect to the internet, right?
No! Not even close! Muahahahaaaaaa
Let's zoom out. First we need instances.
But before that (so zeroth), we need a place to put them in. See that green box labeled subnet?
Subnets
You can't connect your EC2 instance to an internet gateway directly! Only a subnet can be connected to the internet gateway. You need to put your instance inside a subnet, and connect that subnet to the internet gateway.
A subnet is a way to group your instances. It's sort of like tagging them. Here I have four instances
and now I've tagged them with subnet A or subnet B
To connect an instance to the internet, you need to put it in a subnet that is connected to the internet. Notice I said "put it in a subnet", but the subnet's not like a basket you're putting your instances into. It's just a tag, or a connection. Or an assignment.
Public and private subnets
By default, subnets can't talk to the internet. Subnets without a connection to the internet are called private subnets. Subnets that have a connection to the internet are called public subnets. To get your instance connected to the internet, one of the steps you need to take is assign it to a public subnet.
Sidebar: Why do we need to put our instance in a subnet? Well, we can't just put an instance in a VPC, because remember, the VPC spans all the availability zones in a region. To create an instance, we need to specify which availability zone we want to create the instance in. That way, we can create instances in multiple availability zones, to guard against outages. VPCs are region-scoped, but subnets are availability zone-scoped. To assign our instance an AZ, we assign it a subnet.
Now we have something like this
And to connect to the internet here's what we need:
Everything is ready, but to connect the subnet to the internet gateway, we need a route.
Terraform code for creating a subnet:
resource "aws_subnet" "subnet_name" {
vpc_id = aws_vpc.main.id
cidr_block = "10.0.1.0/24" # see next chapter
}Routes
A route is a connection from your subnet to the internet gateway so that your subnet can talk to the internet.
We need to create a route from our subnet to the internet gateway. To do that, we need to learn two new concepts first: CIDR notation, and route tables. The next chapter will talk about these stimulating concepts.
Summary
An internet gateway is like a hole you poke in your VPC so you can talk to the internet.
You can't connect your EC2 instance to an internet gateway directly. You need to put it in a subnet, and connect that subnet to the IGW.
Subnets without a connection to the internet are called private subnets. Subnets with a connection to the internet are called public subnets.